Take 4 minutes to read this article
GoDaddy Hacking and DDoS Attack: Are You Vulnerable?
How F5 Application Security Manager Stops DDoS Attacks.
GoDaddy.com was attacked on Monday over the course of several hours by a malicious Distributed Denial-of-Service or DDoS attack that temporarily took down all websites hosted by GoDaddy.com and interrupted e-mail communication from anyone using its e-mail services. The hackers bragged about how easy it was to attack GoDaddy’s vulnerable security infrastructure, which begs the question: just how vulnerable is your infrastructure to a similar, if not worse, attack? Monday’s attack demonstrates that there are still major companies that remain unprotected against DDoS attacks. You don’t have to be one of them.
CentricsIT recommends deploying F5 Networks’ Application Security Manager to protect your infrastructure from a DDoS attack. We’re breaking down how an F5 BIG-IP device equipped with Application Security Manager (ASM) would handle a DDoS attack of this magnitude.
Because the F5 BIG-IP acts as a fully proxy architecture, it acts as a strategic point of control and gives network and security administrators much better insight into their traffic. The F5 Application Security Manager takes advantage of this proxy architecture to deflect any network attack. The process works in three phases: Detect, Identify, and Mitigate.
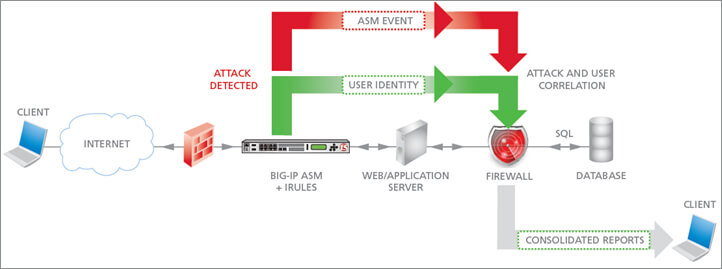 F5 ASM During a Network Attack.
F5 ASM During a Network Attack.
Detect:
F5 uses anomaly detection to analyze traffic and detect potentially malicious patterns on your network and breaks them down into one of four categories:
- Denial-of-Service (DoS) Attacks: Detects the spikes and anomalies in Layer 7 (application layer) traffic. This is the type of attack that GoDaddy.com experienced.
- Brute Force Attacks: Protects against a hacker’s forceful attempts to gain access to a website.
- Increased Violations from Specific IP Addresses: Prevents attacks originating from specific IP addresses.
- Bot Detection and Web Scraping: Prevents automated extraction of data from websites.
These types of attacks typically originate from large groups of zombie computers known as botnets, and typical botnet behavior sends up warning flares to an F5 BIG-IP device. Because the F5 BIG-IP interacts at the application layer (layer 7) and keeps tabs on the applications that it protects, it is able to determine what ‘normal’ behavior is for legitimate application access. F5 is then able to use a variety of heuristic methods to detect an incoming DDoS attack by analyzing events that are out of scope with typical performance. These behaviors can include access rate over time (looking for heavy traffic at off-peak times), application responses (looking for an increase in 404 and 500 errors), and geographic traffic patterns (looking for increased traffic from an unexpected geo).
Identify:
Once the traffic anomalies have been analyzed, and a confirmed DDoS event is taking place, the next step is to identify the offending bot traffic and separate it from legitimate traffic. The F5 BIG-IP ASM provides several solutions. A less intrusive method employed by the ASM is an injection of JavaScript to the requester. This will distinguish browser traffic from more automated bots tools because most bots cannot process JavaScript code (Although Google has been doing this for some time). This can present an issue if legitimate users do not have JavaScript enabled in their browsers. Thankfully, the F5 ASM employs additional methods of identifying and sorting threats, such as challenging all incoming traffic with a CAPTCHA authentication test. This allows humans to be sorted from bots through a random and personalized process. This would be ideally placed on a login page or some other reasonable break point in your application.
Mitigate:
Using the information obtained through the Detect and Identify phases, the F5 BIG-IP ASM is able to mitigate the attack and prevent further disruption of your critical web applications by dropping or delaying the offending connections. Dropping connections results in a simplified mitigation strategy, but it’s a very black and white answer to a grey problem. Even with all of this analysis, false positives are still possible and expected. A better solution is to reduce the request rate from suspect sources to a maintainable level. Even in a worst case scenario, though with somewhat slower access to a legitimate user, the F5 BIG-IP with ASM is able to do the most important thing: maintain application availability. The BIG-IP also offers detailed reporting during the DDoS event to provide you with a much more complete understanding of what exactly is taking place on your network, so that you can make confident security decisions.
No prevention and mitigation strategy is perfect, but the F5 BIG-IP equipped with ASM delivers a robust solution that enables you to Detect, Identify and Mitigate incoming DDoS attacks quickly. Through a combination of packet-level application awareness, robust scalability, and detailed analysis, the F5 BIG-IP can prevent you from falling victim to a DDoS attack in the way that GoDaddy.com did on Monday.
If you have any questions about F5 ASM or any other network security devices, submit it in the comments below or contact us today. CentricsIT is an F5-Certified Gold Partner. We are network experts trained by F5 and operate the website adapture.com.




